
What is OSINT in cyber security? It’s the use of Open Source Intelligence to protect networks by analyzing public data like websites, social feeds, and leaked files. Instead of relying on private data, OSINT finds insights in the open digital world.
This approach has become vital to modern cybersecurity best practices. With increasing cyber threats, OSINT helps teams gather reliable cyber threat intelligence quickly—making it a powerful tool for defense and prevention.
1. What is OSINT?
What is OSINT in cyber security? At its core, it stands for Open Source Intelligence – the process of collecting and analyzing publicly available information to support decision-making, especially in the field of cybersecurity.

In the context of OSINT cybersecurity, it’s not just about gathering information. It’s about turning that information into something useful. Security teams rely on OSINT to detect threats, assess risks, and build stronger defenses. The real value comes from transforming raw data into actionable intelligence—insights that are timely, relevant, and trustworthy.
Not all data is equal. Raw data is unfiltered and can be overwhelming. Actionable intelligence, on the other hand, is carefully selected, verified, and put into context to support specific goals—like identifying a data breach or detecting a phishing campaign.
There are many types of OSINT sources, including:
- Publicly available documents (e.g., research papers, whitepapers)
- Websites and online databases
- Social media platforms (e.g., Twitter, LinkedIn)
- Media reports and news outlets
- Government publications and public records
- Online forums and community boards
- Domain registration data (WHOIS)
- Code repositories (like GitHub)
These sources help cybersecurity professionals collect the right information to monitor threats, investigate incidents, and strengthen their defense strategies. Open Source Intelligence has become a cornerstone of modern cyber threat analysis, offering a proactive approach to staying ahead of potential attacks.
Read more >>> What is End of Life Software? Risks & Best Practices for EOL Management
2. How OSINT works
To truly understand what is OSINT in cyber security, it’s important to look at how it actually works. OSINT is more than just searching Google. It follows a structured process that helps turn open information into useful cyber threat intelligence.

Here’s a quick breakdown of the key stages:
1. Identifying information needs
It starts with a question or goal. What threat are you trying to detect? What do you need to know? Defining this helps guide what kind of data to collect.
2. Data collection
Analysts gather data from various Open Source Intelligence sources—like websites, forums, social media, or public records. Tools such as Shodan or theHarvester often assist in this step.
3. Data processing
Once collected, the data is cleaned and organized. This step removes noise and focuses only on the information that matters.
4. Analysis
Analysts look for patterns, connections, or anomalies. This is where raw data becomes actionable intelligence, helping identify potential cyber threats.
5. Dissemination
The final insights are shared with decision-makers, security teams, or clients. This allows organizations to take action—whether it’s patching a vulnerability or launching an investigation.
In short, the power of OSINT cybersecurity lies in its method. By following a clear process, professionals can use publicly available data to improve cybersecurity best practices and respond to threats before they cause harm.
Read more >>> What is Platform as a Service (PaaS)? Advantages, Disadvantages, Core Features
3. OSINT methodologies
Understanding what is OSINT in cyber security goes beyond just knowing what it means. It’s also about how it’s done. OSINT relies on structured methods and reliable OSINT tools to turn public data into useful insights.
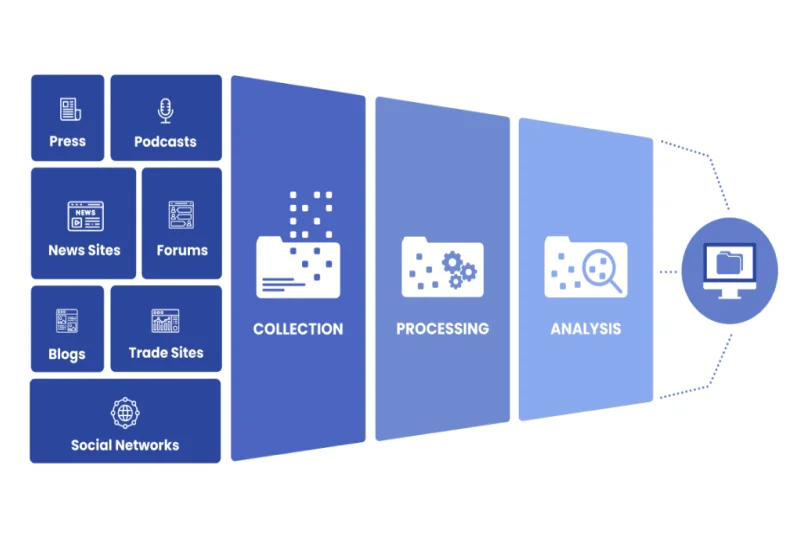
3.1. Common OSINT collection techniques
Professionals use several methods to collect data:
- Web scraping: Automatically gathers information from websites and online platforms.
- Search engine optimization (SEO) techniques: Helps find specific data using advanced search queries.
- Social media analysis: Tracks posts, comments, and behaviors on platforms like Twitter, Facebook, or LinkedIn.
- Dark web monitoring: Detects leaks or malicious activity in hidden forums.
- Geospatial intelligence: Uses maps and satellite imagery for location-based insights.
- Human intelligence: Relies on tips or firsthand information from people.
These techniques help collect large amounts of data, but that’s just the first step.
3.2. From data to intelligence
After collecting the data, analysts need to verify and analyze it. This includes:
- Validating sources to ensure the information is accurate
- Removing duplicate or misleading data
- Identifying patterns, links, or threats
- Matching findings with known indicators of compromise (IOCs)
This process transforms raw data into trusted cyber threat intelligence, which security teams can act on.
3.3. Step-by-step guide to conducting OSINT investigations
Here’s a step-by-step guide to conducting OSINT investigations in cybersecurity:
1. Define your goal
Start with a clear question. What are you trying to uncover—data breaches, leaked credentials, exposed devices?
2. Choose your tools
Select the right OSINT tools like Shodan, Maltego, or theHarvester based on your objective.
3. Collect data
Use the chosen techniques to gather information from open sources.
4. Process the data
Clean and organize what you’ve collected for easier analysis.
5. Analyze for insights
Look for connections, red flags, and security risks.
6. Validate the findings
Cross-check with other data points or known threat indicators.
7. Document and share
Create a report and distribute it to the right team members or departments.
By following this method, OSINT cybersecurity investigations become more effective and reliable, helping organizations stay ahead of emerging cyber threats.
4. Popular OSINT tools

To fully grasp what is OSINT in cyber security, it’s essential to explore the tools that make it all possible. OSINT tools help cybersecurity professionals gather, analyze, and visualize public data quickly and effectively. Here are some of the most widely used tools in the field.
Read more >>>> What is Computer-aided Software Engineering (CASE)? | 10 Type of CASE
4.1. Maltego
Maltego is a powerful tool for link analysis and mapping relationships between data points. It’s widely used to visualize how people, domains, IPs, and organizations connect. With its drag-and-drop interface and built-in data connectors, Maltego makes it easy to spot hidden links during investigations. It’s perfect for uncovering complex networks in cyber threat intelligence work.
4.2. Shodan
Shodan is like a search engine for internet-connected devices. It scans the web for open ports, servers, webcams, routers, and more. Security teams use it to find vulnerable systems exposed to the internet. This makes Shodan a crucial part of any OSINT investigation, especially for identifying risks in your own infrastructure or spotting misconfigured systems globally.
4.3. Recon-ng
Recon-ng is a command-line tool built for automated reconnaissance. It’s modular, meaning you can plug in different features depending on your needs. It supports gathering data like usernames, domains, IP addresses, and even social media profiles. Its automation saves time, especially during large-scale OSINT projects.
4.4. theHarvester
theHarvester specializes in gathering email addresses and subdomain information from public sources. It scans search engines, databases, and other online directories to collect valuable contact data. This tool is especially useful in early-stage information gathering and cyber threat analysis.
Each of these OSINT tools serves a unique purpose, but together they provide a solid foundation for building strong OSINT cybersecurity strategies. Whether you’re analyzing networks with Maltego, finding exposed devices using Shodan, automating tasks with Recon-ng, or collecting contact data via theHarvester, these tools help transform raw data into real, actionable intelligence.
Read more >>> Commercial Off-the-Shelf (COTS) Software | Definition, Benefit, Drawbacks
5. Applications of OSINT in cybersecurity
To understand what is OSINT in cyber security, you also need to see how it’s used in real-world scenarios. Open Source Intelligence is more than just a toolset—it plays a strategic role in defending organizations against digital threats. Let’s break down its core applications.
5.1. Threat intelligence gathering
One of the main uses of OSINT is in cyber threat intelligence. By monitoring public sources like forums, social media, and the dark web, security teams can detect early signs of planned attacks or data leaks. This gives organizations a chance to prepare and respond before damage occurs. It’s also useful in tracking hacker groups and spotting trends in cybercrime.
5.2. Vulnerability assessment
How does OSINT enhance cybersecurity measures? One way is through vulnerability assessment. OSINT helps identify exposed systems, outdated software, or weak configurations by scanning open sources like Shodan or public code repositories. This allows teams to fix security gaps before attackers exploit them. It’s a low-cost way to stay proactive.
5.3. Incident response and investigation
After a breach or suspicious event, OSINT becomes a valuable asset in incident response and investigation. Analysts can use tools like Maltego or theHarvester to map connections, trace attackers, or gather digital footprints. It speeds up the investigation and helps determine the scope of the incident.
5.4. Enhancing cybersecurity best practices
Understanding the role of OSINT in cyber threat intelligence shows how it supports smart decision-making. It empowers organizations to develop stronger defenses, monitor risks continuously, and react faster to threats. This aligns perfectly with cybersecurity best practices like real-time monitoring, regular risk assessments, and informed policy updates.
In short, OSINT provides visibility. It helps security teams stay a step ahead by using publicly available data to detect threats, assess weaknesses, and investigate incidents. That’s why it’s become a critical component of any modern OSINT cybersecurity strategy.
6. Conclusion
So, what is OSINT in cyber security really about? It’s about turning publicly available data into valuable insights that help protect systems, people, and organizations. From identifying threats to investigating incidents, Open Source Intelligence plays a crucial role in modern cyber threat intelligence.
As cyberattacks grow more sophisticated, the importance of OSINT cybersecurity will only increase. We can expect future trends to include more automation, deeper integration with AI, and stronger focus on dark web and social media monitoring. Organizations that invest in OSINT today will be better prepared to face tomorrow’s threats.




